One Email. Two Billion Downloads. Zero Alerts.
If you’re a CTO or CISO, you probably felt the tremor before the headlines broke.
On September 8, 2025, a single phishing email granted attackers access to the npm account of a trusted open-source maintainer. Within hours, 18 of the most widely used JavaScript packages were compromised. Together, they accounted for over 2 billion weekly downloads. Not monthly. Weekly.
The infection vector? A simple social engineering ploy disguised as a support email from npm. It tricked the maintainer into resetting 2FA, handing attackers full access.
The consequence? Every app that depended on packages like chalk, debug, ansi-styles, and has-flag suddenly shipped malware to its users. CI/CD pipelines didn’t blink. Dependency bots auto-upgraded. No one noticed.
Until browser wallets started draining.
The Trojan Was Already Inside the Castle
Here’s what made this attack different: there was no exploit in the code you wrote. The poison was embedded in the code you inherited, the packages your build scripts silently depend on.
The attackers moved quickly:
- Injected obfuscated code into chalk and its transitive dependencies.
- Leveraged legitimate-looking version bumps to pass unnoticed.
- Ensured functionality remained unchanged, so downstream apps wouldn’t throw errors.
chalk alone is a dependency of over 90,000 public GitHub repositories. That includes testing frameworks, CLI tools, and DevOps scripts. It wasn’t just one app that got infected. It was the entire JavaScript universe.
And here’s the kicker: none of these packages looked suspicious. They passed syntax checks. They passed linters. They passed your deployment gates. Because the new versions were signed and published by a legitimate maintainer.
The Browser Is the New Hot Wallet
Once inside, the malicious code did something devilishly subtle: it waited for execution in front-end environments.
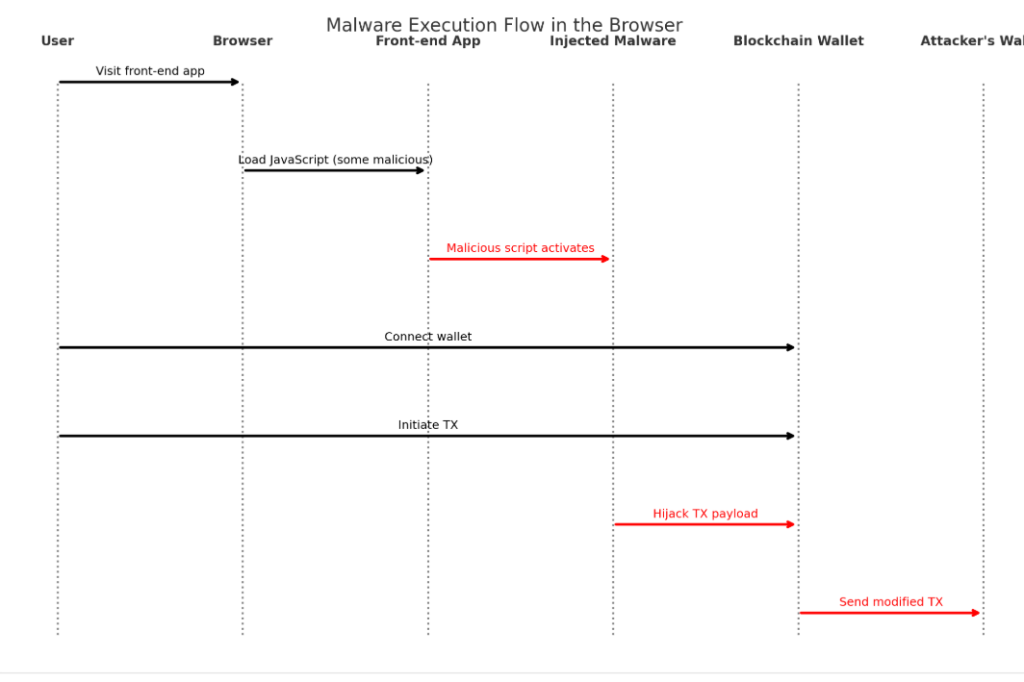
When apps imported the compromised packages and rendered browser-facing components, the malware activated. It scanned for common Web3 wallets (MetaMask, Phantom, Rabby), hooked into transaction prompts, and quietly redirected funds to attacker-controlled addresses.
This wasn’t a backdoor. It was a browser-side man-in-the-middle. Users were still clicking “Approve” on legit-looking prompts. But the destination had changed.
Security researchers estimate the exploit was live for just under 2 hours before npm took down the malicious versions. But in those 2 hours, tens of thousands of builds had already baked in the malware.
Auto-Updates Just Became a Liability
Dependency managers did their job, which was the problem. Tools like Renovate and Dependabot upgraded projects to the latest semver-compatible versions without human review. CI/CD pipelines compiled and shipped production builds as usual.
No alerts were triggered. No AV flagged the behavior. Static analysis missed it. Why? Because the code didn’t look malicious. It only behaved maliciously at runtime, in the browser, under very specific wallet interaction conditions.
We now have to accept a sobering truth: your supply chain is only as strong as the human behind the package. One compromised maintainer account can cascade into millions of compromised apps.
From OSS to OSSINT: A Founder’s Supply-Chain Playbook

For founders and CXOs building in Web3, this attack marks a turning point. The old assumptions, that package managers are trustworthy, that dev tooling is safe by default, that upstream attacks are rare, are now obsolete.
Here’s what must change:
1. Pin Dependencies. Audit Lockfiles.
Stop blind-upgrading. Use exact versions and hash-locked integrity files. Run retroactive diff scans before merging upgrades.
2. Enforce Maintainer Hardening
All critical package contributors must use hardware-backed 2FA, monitored logins, and restricted publishing IPs.
3. Invest in Runtime Behavior Scanning
Static tools won’t catch this. Adopt anomaly detection platforms that simulate runtime behavior in browser sandboxes.
4. Build Rollback Playbooks
Have a plan to revert infected builds across your infrastructure fast. That includes invalidating CDN caches and alerting users.
5. Support Sigstore & Verified Builds
Push the ecosystem toward cryptographic package signing, so provenance can be independently verified.
From Incident to Inflection Point
This wasn’t just another npm scare. It was a billion-download incident. And it’s only the beginning.
The attackers didn’t need to breach your servers. They didn’t need to find a zero-day. They just needed one maintainer to click the wrong link. The rest? Supply chain physics.
In this new era, your most critical security layer isn’t your firewall. It’s your build process.
Don’t just patch the tools. Rethink the trust.